Using AWS for uploading media
We offload assets to S3 for scalability. Here's how you set it up.
Assets on Rooftop are offloaded to S3 and served through a CDN. If you're using our agency plan, we'll host them on our S3 bucket; if you're using our hosted or open-source plans you'll need to create your own S3 bucket.
Setting up S3 on the hosted plan
On the hosted plan, you need to store your assets in your own S3 bucket, but we'll deliver them through a CDN for you (at our expense) so you'll only pay a fraction of the data transfer fees you would otherwise.
Use the EU-WEST1 zone
Buckets must be created in the EU-WEST1 AWS region at the moment. That's because we have some code which creates a CNAME record for you on our
rooftop.iodomain, and it assumes this. There is an open ticket to make this more flexible.There's no issue with using EU-WEST1 even if the majority of your visitors are elsewhere - we proxy the content through a CDN anyway.
Create your S3 user with permissions to manage a bucket
You need to create an IAM user your AWS account with permission to manage your content bucket.
Set a policy for the user
You should limit your IAM user to just managing a specific bucket, because you'll be using these credentials in the Rooftop CMS admin interface.
Here's the policy you need:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:DeleteObject",
"s3:GetObject",
"s3:GetObjectAcl",
"s3:ListBucket",
"s3:PutObject",
"s3:PutObjectAcl",
"s3:GetBucketLocation",
"s3:CreateBucket"
],
"Resource": [
"arn:aws:s3:::yoursubdomain.rooftop.io",
"arn:aws:s3:::yoursubdomain.rooftop.io/*",
"arn:aws:s3:::yousubdomain.rooftop.io",
"arn:aws:s3:::yoursubdomain.rooftop.io/*"
]
}
]
}
Make a note of the IAM user's access key ID and secret access key
Create an access key ID and secret access key, and make a note of them. You'll need them in the next step.
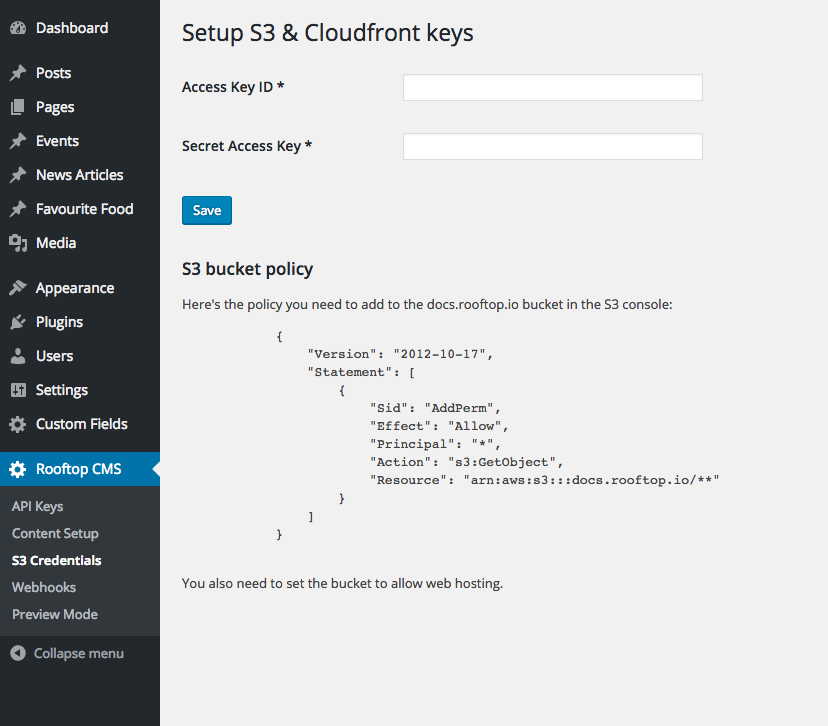
Add your credentials to your Rooftop account
Log into your Rooftop CMS account and navigate to the Rooftop CMS => S3 Credentials page. Complete the form and hit save.
If you have the correct permissions for your IAM user, the page will update. If not, you'll get a (hopefully helpful) error.
What happened when I saved my keys?
Rooftop did 2 things when you saved your keys (provided your IAM user had the correct permissions in S3):
- A bucket was created, called
yoursubdomain.rooftop.io - note rooftop.io not rooftopcms.io- A CNAME record was added in the rooftop.io domain, which points to your bucket.
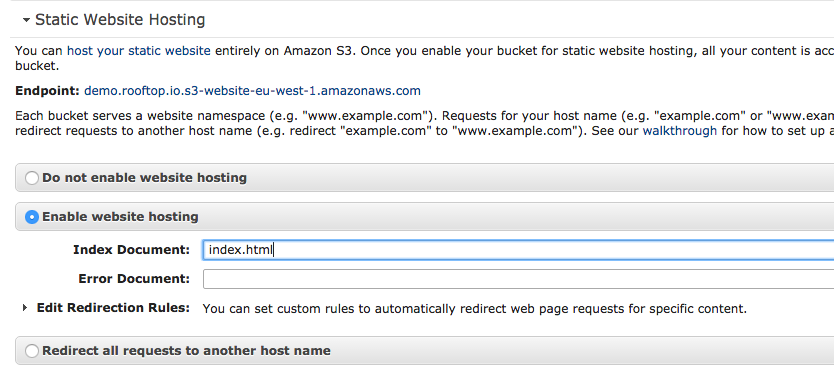
Set permissions and web hosting on your bucket
Go back to the S3 console and set up permissions for the bucket. The permissions are shown on the S3 configuration page in Rooftop:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AddPerm",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::yoursubdomain.rooftop.io/**"
}
]
}
You also need to set static webhosting 'on' in the S3 console:
## You're done!
When you upload media or attachments to Rooftop, you'll see that the url is yoursubdomain.rooftop.io.
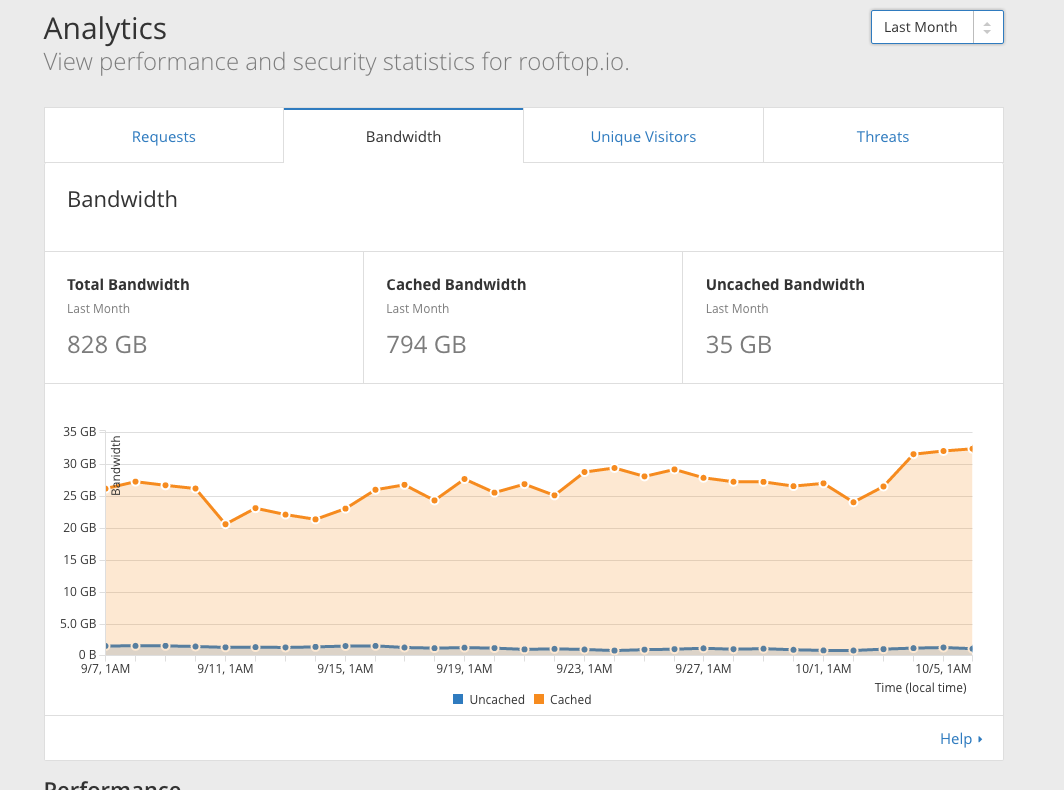
A bit more info on the CDN
We use Cloudflare in front of your S3 buckets for caching and delivery. We absorb this cost as part of the hosted service. It means you'll see a bill for a fraction of actual data transfer. As an illustration, here's the month of September 2016 for our hosted clients:
Setting up S3 for a self-hosted Rooftop CMS setup
Rooftop makes use of the WP Offload S3 plugin, which you'll need to configure to point to your bucket as appropriate. Because Rooftop CMS is multisite, we have a master AWS key/secret set, and then one for each site. You'll need to replicate this setup.
The rest of the docs above should work as you'd expect.
Updated over 4 years ago
